Jump to
Demystifying Attack Path Mapping
Staying ahead of potential threats for organizations requires a proactive approach. Cyber security professionals employ attack path mapping to understand, visualize, and mitigate potential attack vectors within a system or network. Regarding exposure management, attack path mapping helps shortlist the most critical findings out of hundreds or thousands of findings and thus reduces the company’s risk level.
At its core, attack path mapping involves the identification and analysis of potential routes that a cyber attacker could take to infiltrate a target system or network. These paths typically consist of a series of interconnected steps or vulnerabilities that, when exploited, enable unauthorized access or compromise of sensitive assets.
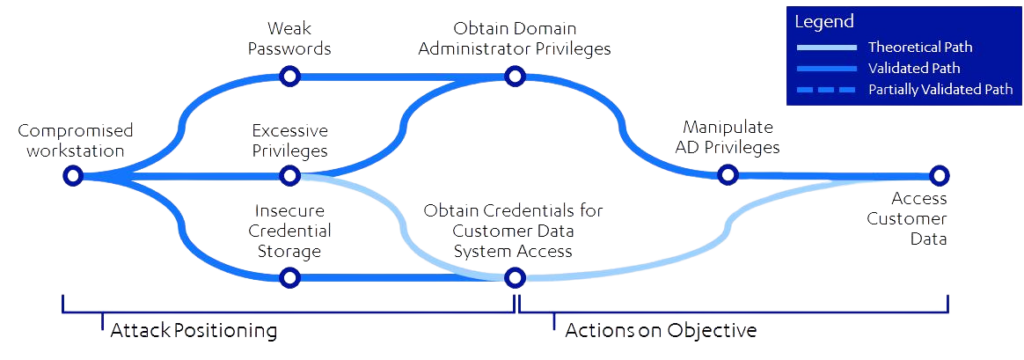
The process of attack path mapping begins with thorough reconnaissance and enumeration, where security experts gather information about the target environment, including its infrastructure, applications, protocols, and potential vulnerabilities. This information is the foundation for constructing a comprehensive map of potential attack paths.
Key Benefits
Attack path mapping offers several key benefits in the realm of cyber security defense:
- Risk Assessment: When performing a risk assessment, it’s important to do so in the context of your business, i.e., how critical is the asset for the company, and what is the possible impact? Organizations can assess the likelihood and impact of various cyber threats by visualizing potential attack paths. This allows them to prioritize security measures and allocate resources effectively to mitigate the most critical risks.
- Vulnerability Identification: Attack Path Mapping helps uncover hidden vulnerabilities and weak points within a system or network architecture. By understanding how these vulnerabilities can be exploited in tandem, organizations can take proactive steps to remediate or patch them before malicious actors exploit them.
- Incident Response Planning: With insights from attack path mapping, organizations can develop more effective incident response plans. By anticipating potential attack scenarios and their corresponding paths, security teams can respond swiftly and decisively to mitigate the impact of security breaches.
- Compliance and Regulation: Many industry regulations and compliance standards require organizations to demonstrate a proactive approach to cyber security risk management. Attack Path Mapping provides a structured methodology for fulfilling these requirements by identifying and addressing potential security gaps.
Best practices
To effectively leverage Attack Path Mapping in their cyber security defense strategies, organizations can follow these best practices:
- Continuous Monitoring: Cyber threats are constantly evolving, making continuous monitoring essential for staying ahead of potential risks. Regularly updating and revisiting attack path maps ensures organizations remain vigilant against emerging threats and vulnerabilities.
- Collaboration and Communication: Attack Path Mapping is a collaborative effort that involves multiple stakeholders, including security analysts, network administrators, and business leaders. Effective communication and collaboration facilitate sharing insights, expertise, and resources necessary for comprehensive threat mitigation.
- Automation and Tools: Automation tools can streamline the Attack Path Mapping process by aggregating and analyzing vast amounts of data more efficiently than manual methods. Investing in advanced threat intelligence platforms and network visualization tools can enhance the accuracy and effectiveness of Attack Path Mapping efforts.
- Adaptability and Flexibility: Cyber attackers are adept at adapting their tactics to circumvent security measures, making it crucial for organizations to remain adaptable and flexible in their defense strategies. Regularly updating attack path maps and reassessing security controls ensures that defenses remain resilient against evolving threats.
The ability to anticipate, detect, and mitigate cyber threats is paramount in today’s interconnected digital landscape. Attack Path Mapping provides organizations with a proactive framework for understanding and addressing potential security risks, enabling them to fortify their defenses against increasingly sophisticated cyber attacks.
By embracing attack path mapping as a core component of their cyber security strategy, organizations can enhance their resilience and safeguard their critical assets in the face of evolving threats.